| |
Advanced Onion Router
|
Advanced Onion Router is a client for the OR network and is intended to be an improved alternative for Tor+Vidalia+Privoxy bundle for Windows users.
Before trying Advanced Onion Router, try the original Tor client (https://torproject.org) and read the available documentation to get familiar with Onion Routing and OR Network. You may find Vidalia easier to use.
| | | Tor is free software and an open network that helps you defend against a form of network surveillance that threatens personal freedom and privacy, confidential business activities and relationships, and state security known as traffic analysis.
Tor protects you by bouncing your communications around a distributed network of relays run by volunteers all around the world: it prevents somebody watching your Internet connection from learning what sites you visit, and it prevents the sites you visit from learning your physical location. Tor works with many of your existing applications, including web browsers, instant messaging clients, remote login, and other applications based on the TCP protocol.
Hundreds of thousands of people around the world use Tor for a wide variety of reasons: journalists and bloggers, human rights workers, law enforcement officers, soldiers, corporations, citizens of repressive regimes, and just ordinary citizens. See the Who Uses Tor? page for examples of typical Tor users. See the overview page for a more detailed explanation of what Tor does, and why this diversity of users is important.
Tor doesn't magically encrypt all of your Internet activities, though. You should understand what Tor does and does not do for you. |
|
|
Some of the improvements of Advanced Onion Router include support for HTTP/HTTPS proxy on the same Socks4/Socks5 port, a User Interface which makes all Tor available options more accessible, local banlist for forbidden addresses, the ability to "force" a program and its extensions / plugins to use the Tor proxy regardless of its configured proxy settings, and more. To reduce the elements that can be used by an attacker to relate different identities (OR vs. non-OR, OR vs. OR), many new features were introduced and many more will be implemented.
Download locations:
|
License
|
Advanced Onion Router consists of Tor 0.2.1.30, Graphical Interface and extensions.
- Tor is distributed under this license:
Copyright © 2001-2004, Roger Dingledine
Copyright © 2004-2006, Roger Dingledine, Nick Mathewson
Copyright © 2007-2013, The Tor Project, Inc.
Redistribution and use in source and binary forms, with or without modification, are permitted provided that the following conditions are met:
- Redistributions of source code must retain the above copyright notice, this list of conditions and the following disclaimer.
- Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following disclaimer in the documentation and/or other materials provided with the distribution.
- Neither the names of the copyright owners nor the names of its contributors may be used to endorse or promote products derived from this software without specific prior written permission.
- This product includes software developed by the OpenSSL Project for use in the OpenSSL Toolkit (http://www.openssl.org/), zlib (http://www.zlib.net/) and libevent (http://www.monkey.org/~provos/libevent/).
- Graphical Interface, extensions added to Tor client and AdvOR.dll are distributed under Creative Commons Attribution - NonCommercial - ShareAlike license.
Copyright © by Albu Cristian, 2009-2013
Disclaimer: This software is provided by the copyright holders and contributors "as is" and any express or implied warranties, including, but not limited to, the implied warranties of merchantability and fitness for a particular purpose are disclaimed. In no event shall the copyright owner or contributors be liable for any direct, indirect, incidental, special, exemplary, or consequential damages (including, but not limited to, procurement of substitute goods or services; loss of use, data, or profits; or business interruption) however caused and on any theory of liability, whether in contract, strict liability, or tort (including negligence or otherwise) arising in any way out of the use of this software, even if advised of the possibility of such damage.
|
Starting Advanced Onion Router
|
By default, the executable file name is AdvOR.exe . All language files must be named [exe_file_name]-[language].lng .
If the executable file is renamed, all the files and sub-directories that have the word "AdvOR" as prefix must be renamed, the new names will have the prefix "AdvOR" replaced with the new name that was set for "AdvOR.exe". This allows more different versions of AdvOR to exist in the same directory with different prefixes. For example, when renaming "AdvOR.exe" to "NewFileName.exe", the following file names can be used:
| Old file name | New file name |
|---|
| AdvOR.exe | NewFileName.exe |
| AdvOR.dll | NewFileName.dll |
| AdvOR-plugins | NewFileName-plugins |
| AdvOR.log | NewFileName.log |
| AdvOR-English.lng | NewFileName-English.lng |
| AdvOR-cached-certs | NewFileName-cached-certs |
| AdvOR-cached-consensus | NewFileName-cached-consensus |
| AdvOR-cached-descriptors | NewFileName-cached-descriptors |
| AdvOR-cached-descriptors.new | NewFileName-cached-descriptors.new |
In this document, when referring to files related to Advanced Onion Router, default file names will be used.
To start Advanced Onion Router execute AdvOR.exe . To use AdvOR as a proxy or as a server click "Connect".
More instances of AdvOR can be started if they are started from different directories and their proxy ports are different. Instead of starting more AdvOR instances, consider using exclusivity for different processes that are not allowed to have their traffic redirected to the same exit node (see the Sandboxing settings).
|
Basic Commands

|
| Displayed name | Action |
|---|
 | Select a window created by a process that will be intercepted.

The button "»" opens the "Quick Start" and the "Release" menus. |
| Connect / Disconnect | Connect to the OR network or disconnect from the OR network. To use Advanced Onion Router as a proxy or as a server it must be connected to the OR network.
AdvOR is successfully "connected" to the OR network (bootstrap status 100%) when an OR circuit was built successfully or when the maximum number of predicted circuits is set to 0. |
| New identity | Change all internal variables that are related to current identity. Optionally, all circuits are expired and/or all connections are closed. Also, some identity-specific information (like HTTP cookies, Flash cookies, uinque identifiers, etc.) can be changed/expired/removed. For more information, see the "Private identity" settings. This command can also be accessed using hot keys.
The button "»" opens a dialog with advanced settings related to how the new exit node is chosen.

| Displayed name | AdvOR.ini value | Action |
|---|
| Country | | A drop-down list with all the country names that were imported from the GeoIP database. There are 2 special entries,- Random country = a random exit node from a random country will be selected.
- No exit = AdvOR is used only to report what a program would do so nothing will be sent through the OR network; no new circuits will be created.
Exit nodes that are banned in MaxMind"s GeoIP database have their countries marked with an asterisk. |
| Node list | | A list of exit nodes from the country that is selected. When the entry "Random country" is selected, this list will have all available nodes. The nodes that are banned are placed at the end of this list. The list can be sorted by country, address, nickname or bandwidth, in ascending or in descending order. |
| Close all existing connections | IdentityFlags | Close all connections and destroy all circuits to prevent mixing traffic that belongs to different identities. |
| Expire tracked hosts | IdentityFlags | Re-map all temporary address maps to new exits. |
| Exit selection algorithm uses consecutive nodes from this list | IdentityFlags | Every time the "New identity" button is clicked, the next node is chosen as a single usable exit (except when using exclusivity keys). The sort order determines which will be the next chosen exit. |
| Use only recent exits that are probably not blacklisted yet | ExitSeenFlags | Some websites that ban Tor and other proxies do not update their blacklists in the moment a new node appears. This allows us to use the newest nodes to access the website until its blacklist is updated. |
| Select | | Change the identity and use the node that is selected as a single exit unless the entry "Random" is chosen which allows one identity to use multiple exits. |
| Add to favorites | ExitNodes | Add the exit that is selected to the list of favorite nodes. When the entry "Random" is selected, the country is added to favorites. |
| Ban selected node | ExcludeExitNodes | Add the exit that is selected to the list of banned nodes. To ban the country that is selected, ban the entry "Random". |
| Cancel | | Closes the exit node selection dialog; all settings that were modified are saved. | |
| Save settings | If possible (when AdvOR was not started from read-only media and/or the "--read-only" parameter was not specified) all settings are saved. When the option to encrypt configuration files is enabled, all settings are saved to an encrypted and compressed file AdvOR.dat (if AdvOR.exe is not renamed). When saving plain-text files, one or more files are written. |
| Always on top | Keep the AdvOR window on top of all other windows, even when a window created by another process is active |
| Minimize to tray | Hide the AdvOr window and add an icon to the system tray. The window can be shown when the system tray icon is clicked. The system tray menus can be accessed with a right click on this icon. The minimize and restore commands can also be accessed using hot keys. |
| Exit | Close all connections, destroy all circuits, save all settings and exit the program. |
|
Proxy Settings

|
| Displayed name | AdvOR.ini value | Action |
|---|
| Proxy port | SocksPort | Advertise this port to listen for connections from applications. Intercepted applications will also redirect all their connection requests to this port. Set this to 0 if you don't want to allow application connections. Default value is 9050. Some applications have default settings to match the defaults from torproject.org for the HTTP port which is 8118, so a good value is also 8118 when using one of these applications that doesn't have a convenient way of changing its proxy settings in realtime. However, the best value is a random value that cannot be guessed or obtained with a simple port scan.
All proxy protocols are supported (Socks4, Socks5, HTTP, HTTPS).
|
| Proxy address | SocksListenAddress | Bind to this address to listen for connections from applications (default is 127.0.0.1). |
| User:password | SocksAuthenticator
DirFlags | If defined, AdvOR will require this username:password for proxy authentication from all applications that use it. This setting does not affect intercepted processes. |
| Run ... | | Execute a program and intercept it at startup. |
 | | Select a window created by a process that will be intercepted. |
|
Banned Addresses

|
| Displayed name | AdvOR.ini value | Action |
|---|
| Banned ports | RejectPlaintextPorts | Refuse connecting to addresses using specified ports.
The ports from this list must be separated by commas. |
| Banned addresses | BannedHosts | Refuse connecting to addresses from this list.
Each address must be entered on a new line.
The list can be updated from the "OR network" context menus. |
| Reject requests for *.exitname.exit URLs | AllowTorHosts | If this option is enabled, an address like "wwww.google.com.Amunet1.exit" is converted to "www.google.com" that will exit from the node "Amunet1". An attacker can use the ".exitname.exit" feature to manipulate path selection, so the recommended value is 512. Accepted values: 0, 1 |
| Reject requests for *.onion URLs | AllowTorHosts | When this option is enabled, accessing hidden services (*.onion addresses) is disallowed. An attacker can use a hidden service to detect the presence of the OR proxy when using proxy chains at exit. If the use of hidden services is not needed, it is recommended to enable this option. Accepted values: 0, 2 |
|
HTTP Headers

|
Most browsers send in HTTP headers information that can be sometimes used to uniquely identify a particular user even when the IP address is changed. This information may include a minor version, revision number, browser release date, some installed extensions in one particular order which may or may not be the latest releases for those extensions, cookies, additional headers that may contain IPs, GUIDs or cookies, a list with all installed languages and other personalizations.
By default, the browser type is automatically detected and the headers are rewritten to remove and/or replace any information can can be used to correlate different identities. Identity seeds are used to decide how the fake information about the web browser is generated; these seeds may change when the identity is changed, causing the generated headers to show in logs of web servers as if they were generated by a different browser having different fake extensions, optionally on a different OS / OS version and from a different country having different regional settings. This is an attempt to make all different identities look different in web server logs. Version 0.3.0.1 of AdvOR can detect and adjust HTTP headers for proxy chains, it supports HTTP chunked transfers and multipart message types.
HTTPS connections are not supported, encrypted HTTP headers are not modified; some information that is removed/replaced by AdvOR in a plain-text HTTP transfer may be leaked via an encrypted HTTPS connection because AdvOR does not attempt to decrypt/reencrypt that traffic. Browser plugins and scripts are also able to leak some real information that is obscured by AdvOR; however, if the browser is intercepted, browser scripts and plugins cannot obtain some real information about the local system.
|
| Displayed name | AdvOR.ini value | Action |
|---|
| Browser type | HTTPAgent |
The browser type can have one of the following values (numeric values can be used when editing AdvOR.ini directly):
- 0 = Original autodetected browser
The brower type is detected automatically and the headers are rewritten to match the structure of the autodetected browser (header types, order, capitalization, etc.).
- 128 = Generated using identity seeds
Every time the identity is changed, a new browser type is chosen and it is used to mask all browsers that use the AdvOR proxy until the identity is changed. For example, if the identity seeds cause the browser "Firefox" to be chosen when using Opera and uTorrent, the headers generated by Opera and uTorrent will look as if they were generated by Firefox.
- 129 = Don't anonymize browser type
Browser's User-agent string is used without any changes.
- 2 = Chrome
Mask all browsers as Chrome.
- 3 = Firefox
Mask all browsers as Firefox.
- 4 = Internet Explorer
Mask all browsers as Internet Explorer.
- 5 = Opera
Mask all browsers as Opera.
- 6 = Safari
Mask all browsers as Safari.
- 11 = Mask a BitTorrent client as uTorrent
Mask all browsers as uTorrent.
- 7 = Bing bot
Mask all browsers as the Bing bot (search engine spider).
- 8 = Googlebot
Mask all browsers as Googlebot (search engine spider).
- 9 = Yahoo! bot
Mask all browsers as Yahoo! bot (search engine spider).
- 10 = Yandex bot
Mask all browsers as Yandex bot (search engine spider).
Web spiders were included because some websites that make their content available for search engines require payment or registration from normal users to access (this is a SEO technique called "cloaking"). |
| Browser version | HTTPFlags | All browsers send a version number which has one or more components that include a major version number and a minor version number. For example, "Firefox/3.6.12" has the major version number 3 and the minor version 6. To simplify things, Advanced Onion Router uses "6.12" as the minor version number.
The following values are available:
- 128 = Identity-dependent minor version
- 256 = Identity-dependent major version
|
| Browser OS | HTTPOS | Some browsers send information about the operating system type and version they were installed on. Unless the original operating system is selected, the information that will be sent will be fake. Accepted values:- 0 = Original operating system (Windows)
- 1 = Identity-dependent OS (any OS, any version)
- 2 = Identity-dependent Windows (any version)
- 3 = Identity-dependent Linux (any version)
- 4 = Identity-dependent Mac OS X (any version)
|
| Browser extensions | HTTPFlags | The information about browser extensions includes installed plugins and toolbars. Available values:- 32 = Hide all extensions
- 64 = Identity-dependent fake extesions
|
| Regional settings | RegionalSettings | Changing this option can affect how a website is displayed. Some websites generate content based on regional settings. Available values:- 0 = Current regional settings
- 1 = Always set US English language
- 128 = Use exit node's language
|
| Referers must be from the same domain | HTTPFlags | The Referer specifies the originating page where a link to the current page was clicked. Allowing only referers from the same domain restricts a website from knowing which search terms were used to reach that website, but doesn't affect navigation through websites from the same domain.
Accepted values: 0, 2 |
| Remove ETag and Last-Modified from response headers | HTTPFlags | An "evercookie" is designed to regenerate the cookies that were deleted by storing the same data in different locations that the browser can access. These storage mechanisms include HTTP ETags (ETag => If-Match, If-None-Match) and the Web history (Last-Modified => If-Modified-Since, If-Unmodified-Since). Accepted values: 0, 4 |
| Remove If-(Un)Modified-Since, If-(None-)Match, If-Range | HTTPFlags | Sending If-Match, If-None-Match, If-Modified-Since, If-Unmodified-Since and If-Range may give information about previously accessed resources allowing an attacker to correlate different identities and to regenerate tracking cookies. Accepted values: 0, 2048 |
| Remove dangerous HTTP headers | HTTPFlags |
The following headers are considered dangerous because they give an attacker enough information to correlate different identities:- Client-IP, Client_IP
- X-Client-IP
- X-Cluster-Client-IP
- X-NAS-IP
- Client-ID
- X-Real-IP
- CUDA_CLIIP
- FFI*
- From
- Mt-Proxy-Id
- UA-*
- UserIP, User-IP
- Username
- X-APN-ID
- X-IMForwards
- x-power-cache
- X-Autopager
- X-CC-ID
- X-NAI-ID
- x-fw2-identity
- X-Proxy-ID
- X-GGSNIP, X-SGSNIP
- x-charging-id
- x-slipstream* (as in "X-SlipStream-Username:")
- x-tickcount
- X-lori-time-1
- X-Teacup
- X-Saucer
- XID
- X-PID
- MSISDN, X-MSP-MSISDN, X-MSP-RAT
- x-up-subno
- x-icap-version
- X-Livetool
- X-IMSI
- X-MSP-AG
- x-insight
- X-D-Forwarder
- Via, X-Via, X-TM-Via, x-bluecoat-via
- X-McProxyFilter
- X-Varnish
- X-Authenticated-User
- X-C4PC-LWPNB-ADDR
- x-codemux-client
- x-ebo-ua
- x-fcck* (as in "X-FCCK:", "X-FCCKV2:")
- x-forwarded-for, x-up-forwarded-for, x-forwarded-host, x-forwarded-proto, x-forwarded-server
- x-network-info (as in "X-Network-Info: TCP, 10.0.0.1"), x-network-type
- x-nokia*
- X-ProcessAndThread (as in "X-ProcessAndThread: iexplore.exe [4660; 5276]")
- x-wap*
- x2-toolbar-data
- YahooRemoteIP* (as in "YahooRemoteIP:", "YahooRemoteIPSig:")
- x-operamini* (as in "X-OperaMini-Features:", "X-OperaMini-Phone-UA:", "X-OperaMini-Phone:", "X-OperaMini-UA:")
Accepted values: 0, 4096 |
| Remove unknown HTTP headers | HTTPFlags | If this option is enabled and the browser sends unrecognized HTTP headers they are removed from request. Accepted values: 0, 8192 |
| Also, remove these headers | BannedHeaders | This list can be used to remove from all requests any known / unknown headers. Enter each header name on a new line. |
| Show requested addresses | HTTPFlags | If this option is enabled, all requested URLs will be shown in the Debug window ("[notice] Downloading from http://..."). Accepted values: 0, 16384 |
| Full headers for requested address | HTTPFlags | All HTTP headers that are sent by a browser are shown in the Debug window as LOG_INFO ("[7] Info") messages. Adjusted HTTP headers are shown as LOG_NOTICE ("[5] Notice") messages. Accepted values: 0, 32768 |
| Show HTTP status | HTTPFlags | If this option is enabled, all HTTP status codes that are received are shown in the Debug window as LOG_NOTICE messages ("Download status: 200 OK"). Accepted values: 0, 65536 |
| Full received headers | HTTPFlags | All HTTP traffic that is received by a browser is shown in the Debug window as LOG_INFO ("[7] Info") messages. Adjusted HTTP headers are shown as LOG_NOTICE ("[5] Notice") messages. Accepted values: 0, 131072 |
|
Connections

|
| Displayed name | AdvOR.ini value | Action |
|---|
| Bandwidth rate | BandwidthRate | A token bucket limits the average incoming bandwidth usage on this node to the specified number of bytes per second, and the average outgoing bandwidth usage to that same value. (Default: 5 MB) |
| Bandwidth burst | BandwidthBurst | Limit the maximum token bucket size (also known as the burst) to the given number of bytes in each direction. (Default: 10 MB) |
| Advertised bandwidth | MaxAdvertisedBandwidth | If set, we will not advertise more than this amount of bandwidth for our BandwidthRate. Server operators who want to reduce the number of clients who ask to build circuits through them (since this is proportional to advertised bandwidth rate) can thus reduce the CPU demands on their server without impacting network performance. |
| Relay bandwidth rate | RelayBandwidthRate | If defined, a separate token bucket limits the average incoming bandwidth usage for _relayed traffic_ on this node to the specified number of bytes per second, and the average outgoing bandwidth usage to that same value. Relayed traffic currently is calculated to include answers to directory requests, but that may change in future versions. (Default: 0) |
| Relay bandwidth burst | RelayBandwidthBurst | Limit the maximum token bucket size (also known as the burst) for _relayed traffic_ to the given number of bytes in each direction. (Default: 0) |
| Bandwidth rate per connection | PerConnBWRate | Long-term bandwidth on a single TLS connection, if set. |
| Bandwidth burst per connection | PerConnBWBurst | Allowed burst on a single TLS connection, if set. |
| ISP traffic limit | AccountingMax | Never send more than the specified number of bytes in a given accounting period, or receive more than that number in the period. For example, with AccountingMax set to 1 GB, a server could send 900 MB and receive 800 MB and continue running. It will only hibernate once one of the two reaches 1 GB. When the number of bytes is exhausted, AdvOR will hibernate until some time in the next accounting period. To prevent all servers from waking at the same time, AdvOR will also wait until a random point in each period before waking up. If you have bandwidth cost issues, enabling hibernation is preferable to setting a low bandwidth, since it provides users with a collection of fast servers that are up some of the time, which is more useful than a set of slow servers that are always "available". |
| Traffic limit availability | AccountingStart | Specify how long accounting periods last. If month is given, each accounting period runs from the time HH:MM on the dayth day of one month to the same day and time of the next. (The day must be between 1 and 28.) If week is given, each accounting period runs from the time HH:MM of the dayth day of one week to the same day and time of the next week, with Monday as day 1 and Sunday as day 7. If day is given, each accounting period runs from the time HH:MM each day to the same time on the next day. All times are local, and given in 24-hour time. (Defaults to "month 1 0:00".) |
| Maximum number of connections | ConnLimit | The minimum number of file descriptors that must be available to the AdvOR process before it will start. AdvOR will ask the OS for as many file descriptors as the OS will allow. If this number is less than ConnLimit, then AdvOR will refuse to start. |
| Ports for services that have long-running connections | LongLivedPorts | A list of ports for services that tend to have long-running connections (e.g. chat and interactive shells). Circuits for streams that use these ports will contain only high-uptime nodes, to reduce the chance that a node will go down before the stream is finished. (Default for Tor: 21, 22, 706, 1863, 5050, 5190, 5222, 5223, 6667, 6697, 8300) |
| Send / recv buffer size | ConstrainedSockets
ConstrainedSockSize | ConstrainedSockSize must be a value between 2048 and 262144, in 1024 byte increments. Default of 8192 is recommended.
If ConstrainedSockets is set, AdvOR will tell the kernel to attempt to shrink the buffers for all sockets to the size specified in ConstrainedSockSize. This is useful for virtual servers and other environments where system level TCP buffers may be limited. If you're on a virtual server, and you encounter the "Error creating network socket: No buffer space available" message, you are likely experiencing this problem.
The preferred solution is to have the admin increase the buffer pool for the host itself via /proc/sys/net/ipv4/tcp_mem or equivalent facility; this configuration option is a second-resort.
The DirPort option should also not be used if TCP buffers are scarce. The cached directory requests consume additional sockets which exacerbates the problem.
You should not enable this feature unless you encounter the "no buffer space available" issue. Reducing the TCP buffers affects window size for the TCP stream and will reduce throughput in proportion to round trip time on long paths. (Default: 0.) |
| Keepalive / idle time for connections | KeepalivePeriod | To keep firewalls from expiring connections, send a padding keepalive cell every NUM seconds on open connections that are in use. If the connection has no open circuits, it will instead be closed after NUM seconds of idleness. (Default: 5 minutes) |
| Use this local IP for outgoing connections | OutboundBindAddress | Make all outbound connections originate from the IP address specified. This is only useful when you have multiple network interfaces, and you want all of AdvOR's outgoing connections to use a single one. |
| Firewall restrictions | FascistFirewall
ReachableAddresses | A list of IP addresses and ports that your firewall allows you to connect to, each rule on a new line. The format is as for the addresses in ExitPolicy, except that "accept" is understood unless "reject" is explicitly provided. For example, 99.0.0.0/8
reject 18.0.0.0/8:80
accept *:80 |
means that your firewall allows connections to everything inside net 99, rejects port 80 connections to net 18, and accepts connections to port 80 otherwise. (Default: 'accept *:*'.) |
|
Advanced Proxy Settings

|
| Displayed name | AdvOR.ini value | Action |
|---|
| Restrict connections only from these IPs or IP ranges | SocksPolicy | Set an entrance policy for this server, to limit who can connect to the SocksPort and DNSPort ports. The policies have the same form as exit policies below. |
| Handshake timeout | SocksTimeout | Let a socks connection wait NUM seconds handshaking, and NUM seconds unattached waiting for an appropriate circuit, before we fail it. (Default: 2 minutes.) |
| Reject application connections where the application is doing a DNS resolve | SafeSocks | When this option is enabled, AdvOR will reject application connections that use unsafe variants of the socks protocol - ones that only provide an IP address, meaning the application is doing a DNS resolve first. Specifically, these are socks4 and socks5 when not doing remote DNS. (Defaults to 0.) |
| Allow non RFC 953 hostnames | AllowNonRFC953Hostnames | When this option is disabled, AdvOR blocks hostnames containing illegal characters (like @ and :) rather than sending them to an exit node to be resolved. This helps trap accidental attempts to resolve URLs and so on. (Default: 0) |
|
OR Network / Network Information
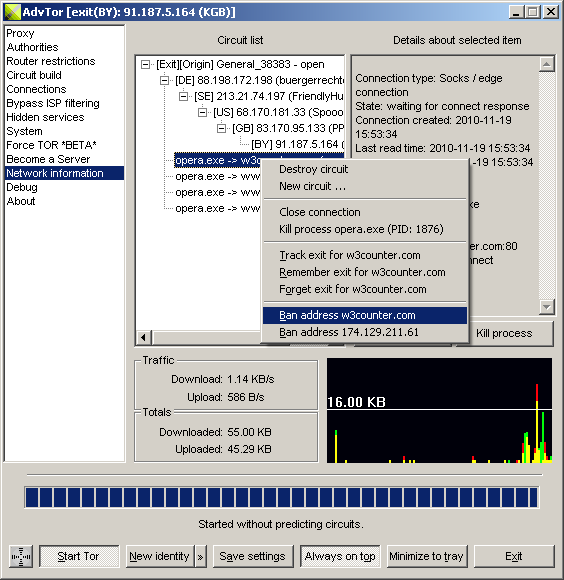
|
| Displayed name | Description |
|---|
| Circuit list | A list of circuits and connections. When possible, the application name that opened a connection is shown. Context menus are available for all items (see the next table). |
| Details about selected item | When an item is selected, this edit box contains more information about that item. |
| Traffic | Current transfer rates for download and upload. The memory unit types are adjusted as needed. |
| Totals | Total number or memory units that were transferred since AdvOR was started. The memory unit types are adjusted as needed. |
| Traffic history | A graphical representation of traffic history (yellow = downloads , red = uploads). The scale is adjusted to make all history items visible. |
Context menus
| Displayed name | Action |
|---|
| Destroy circuit | Destroys the circuit that contains selected item. |
| New circuit ... | Builds a new circuit. For more information, see "Building circuits". |
| Close connection | Close the connection that is selected. |
| Kill process | If the process that opened the connection was identified, an attempt is made to terminate it. |
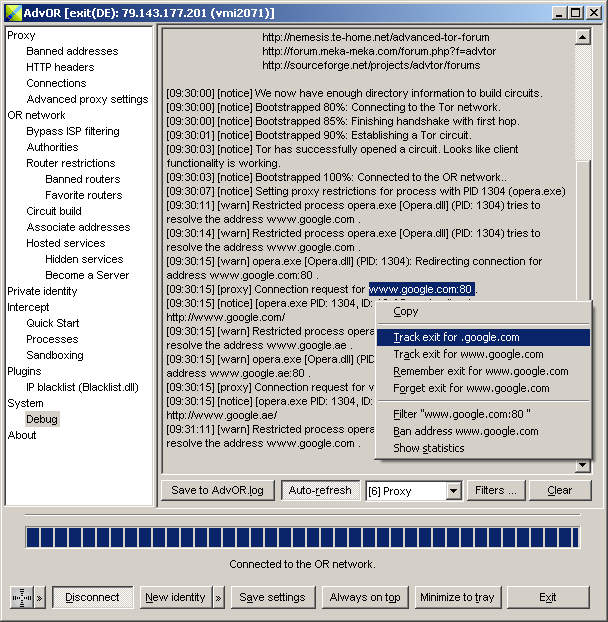
| Track exit for ... | Add an address to the "Associate addresses \ Tracked hosts" list. |
| Remember exit for ... | Add an address to the "Associate addresses \ Exit associations" list. |
| Forget exit for ... | If an association for this address was found in the "Associate addresses \ Exit associations" list, it is removed from that list. |
| Ban address | Add the selected address to the list of banned addresses from the "Proxy" page. |
| Ban ... (all positions | exit) | Add the seelcted node to the "Router restrictions \ Banned routers" list. |
| Mark router ... as invalid | The router is not banned, but it is no longer used to build new circuits until the network status is upaded / reloaded. |
| Add entry|exit ... to favorites | Add the router to the "Router restrictions \ Favorite routers" list |
| Priority | Changes the way a circuit is preferred by new connections. Low priority circuits are avoided when possible. High priority circuits are always the first circuits used for new connections. |
| Availability | Changes the time a circuit is available. A circuit marked as "expired" will be destroyed when all connections that use it are closed. A circuit that never expires is never destroyed unless a network error prevents a node from this circuit from serving requests. |
|
Bypass ISP Filtering

|
| Displayed name | AdvOR.ini value | Action |
|---|
| Use bridge relays | UseBridges | Bridge relays are entry nodes that are not listed in the main Tor directory. When this option is set, AdvOR will fetch descriptors for each bridge listed in the "Bridges" list, and use these relays as both entry guards and directory guards. (Default: 0) |
| Update bridge descriptors from authorities instead of the bridge itself | UpdateBridgesFromAuthority | When set (along with UseBridges), AdvOR will try to fetch bridge descriptors from the configured bridge authorities when feasible. It will fall back to a direct request if the authority responds with a 404. (Default: 0) |
| Get a list of bridges from https://bridges.torproject.org | | The page https://bridges.torproject.org is downloaded and all addresses of bridges are identified and added to the list of bridges and the resulting list is then sorted by country and then by IP.
If downloading the list of bridges fails, it could be because the certification authority used by the certificate from bridges.torproject.org is not recognized by the installed version of Internet Explorer. If this is the case, the download can be retried ignoring unrecognized certification authorities (a message box will ask if the download should be retried ignoring unrecognized certification authorities). |
| Bridges | Bridge | Each bridge must be entered on a new line in the form IP:ORPort [fingerprint] . The list is sorted every time a list of new bridges was downloaded or when the list of bridges was read from AdvOR.ini . If "fingerprint" is provided (using the same format as for DirServer), we will verify that the relay running at that location has the right fingerprint. We also use fingerprint to look up the bridge descriptor at the bridge authority, if it's provided and if UpdateBridgesFromAuthority is set too. |
| All requests will use this NTLM proxy | CorporateProxy
CorporateProxyProtocol
DirFlags | NTLM proxies allow clients to access resources using their Windows credentials, and they are typically used within corporate environments. AdvOR will make all its requests through this host:port (or host:8080 if port is not specified), rather than connecting to other proxies, bridges, directory servers or entry nodes. The NTLM proxy can be chained with ORProxy and/or DirProxy if needed; when enabled, the NTLM proxy is always the first proxy of a proxy chain. Supported protocols: NTLM. |
| [Workstation@]domain | CorporateProxyDomain | If defined, AdvOR will use this workstation@domain for proxy authentication. If the workstation name is not provided, the local hostname is used. |
| Proxy account | CorporateProxyAuthenticator | If defined, AdvOR will use this username:password for proxy authentication. |
| Use encrypted directory connections | TunnelDirConns | Accepted values:
- 0 (unchecked) - don't use encrypted directory connections
- 1 (indeterminate) - when a directory server we contact supports encrypted connections, we will build a one-hop circuit and make an encrypted connection via its ORPort instead of its DirPort.
- 3 (checked) - we will always use encrypted connections and we avoid directory servers that don't support tunneled directory connections, when possible.
Default: 3 |
| All directory actions are private | AllDirActionsPrivate | All directory actions are sent through OR circuits instead of one-hop circuits. |
| All HTTP directory requests will use this proxy | DirProxy
DirProxyProtocol
DirFlags | AdvOR will make all its directory requests through this host:port (or host:80 if port is not specified), rather than connecting directly to any directory servers. Supported protocols: HTTP, HTTPS, Socks4, Socks5. |
| Proxy account | DirProxyAuthenticator | If defined, AdvOR will use this username:password for proxy authentication. This setting is ignored if the proxy protocol doesn't support authentication. |
| All TLS (SSL) connections will use this proxy | ORProxy
ORProxyProtocol
DirFlags | AdvOR will make all its OR (SSL) connections through this host:port (or host:443 if port is not specified), rather than connecting directly to servers. You may want to set FascistFirewall ("Connections \ Firewall restrictions") to restrict the set of ports you might try to connect to, if your proxy only allows connecting to certain ports. Supported protocols: HTTPS, Socks4, Socks5. |
| Proxy account | ORProxyAuthenticator | If defined, AdvOR will use this username:password for proxy authentication. This setting is ignored if the proxy protocol doesn't support authentication. |
|
Authorities

|
| Displayed name | AdvOR.ini value | Action |
|---|
| Directory authorities | DirServers | Use an authoritative directory server at the provided address and port, with the specified key fingerprint. This option can be repeated many times, for multiple authoritative directory servers. Flags are separated by spaces, and determine what kind of an authority this directory is. By default, every authority is authoritative for current ("v2")-style directories, unless the "no-v2" flag is given. If the "v1" flags is provided, AdvOR will use this server as an authority for old-style (v1) directories as well. (Only directory mirrors care about this.) AdvOR will use this server as an authority for hidden service information if the "hs" flag is set, or if the "v1" flag is set and the "no-hs" flag is not set. AdvOR will use this authority as a bridge authoritative directory if the "bridge" flag is set. If a flag "orport=port" is given, AdvOR will use the given port when opening encrypted tunnels to the dirserver. Lastly, if a flag "v3ident=fp" is given, the dirserver is a v3 directory authority whose v3 long-term signing key has the fingerprint fp.
If no dirserver line is given, AdvOR will use the default directory servers. NOTE: this option is intended for setting up a private Tor network with its own directory authorities. If you use it, you will be distinguishable from other users, because you won't believe the same authorities they do. |
| Always select a random directory authority | DirFlags | Switch between sequential and random directory server selection when sending new directory requests. Accepted values: 0, 1 |
| Network information never expires | DirFlags | When this option is enabled, the network information is no longer updated automatically and the only way to update it is the "Refresh network information now" button. Accepted values: 0, 2 |
| Refresh network information now | | Current network information is marked as expired and is updated from the directory servers. |
| Address resolution timeout | ResolveTimeout | Expiration time for all address resolution requests that are sent through the OR network. |
| Wait until at least 3/4 usable descriptors are downloaded | DirFlags | By default, the first circuit is built when 1/4 usable descriptors are enabled. If this option is enabled, AdvOR will download more descriptors before building the first circuit. Accepted values: 0, 4 |
| Never send real information about local time to routers or directory servers | DirFlags | To prevent routers and/or directory servers from using your local time stamp as a cookie to uniquely identify you, enable this option. Accepted values: 0, 16 |
| Randomize "local time" at startup by max ... seconds | MaxTimeDelta | The maximum difference between fake local time and real local time. |
| Also, adjust reported local time to a random router's local time | DirFlags | It is a known fact that Windows users need to change the system time because some applications behave differently if they do so. Normally, Tor requires an accurate clock to work. AdvOR will work with any system time and it will adjust its time delta according to routers and authorities. When changing the system time too far in the future or in the past, this option must be enabled to be able to build circuits and to use them. Accepted values: 0, 32 |
| Maximum router descriptor download failures | MaxDlFailures | Maximum number of retries when downloading router descriptors. |
| Remove cached consensus if it's too old | MaxFileAge | Maximum time the cached consensus can be kept. |
|
Router Restrictions

|
| Displayed name | AdvOR.ini value | Action |
|---|
| Allowed invalid nodes | _AllowInvalid | If some Tor servers are obviously not working right, the directory authorities can manually mark them as invalid, meaning that it's not recommended you use them for entry or exit positions in your circuits. You can opt to use them in some circuit positions, though. The default is "middle,rendezvous", and other choices are not advised. |
| Avoid using in same circuit nodes from same subnets|countries | EnforceDistinctSubnets | If enabled, AdvOR will not put two servers whose IP addresses are "too close" on the same circuit. Two addresses are "too close" if they lie in the same /16 range or if they are in the same country. (Default: 2)
Accepted values: 0, 1 (subnets), 2 (countries) |
| Estimate AS paths and avoid AS path intersections | EnforceDistinctSubnets | If enabled, AdvOR will estimate all possible AS paths between local host and the exit node. If the same AS is found in 2 or more different routes between nodes, the circuit information is discarded and a new circuit is estimated.
As an example, when someone whose AS is AS9050 wants to build the circuit comanche - netfreak - politkovskaja having AS paths for nodes: comanche - AS path: AS4777 -> AS2516 -> AS3549 -> AS21970 -> [AS22047]; netfreak - AS path: AS4777 -> AS2516 -> AS3300 -> AS35590 -> [AS3320]; politkovskaja - AS path: AS4777 -> AS2516 -> AS3549 -> AS43313 -> [AS43350], the following AS paths are estimated:
AS paths:
#1: [AS9050] -> AS35034 -> AS9044 -> AS3257 -> (X)AS2516 -> (X)AS3549 -> AS21970 -> [AS22047] -> AS21970 -> AS3549 -> AS2516 -> AS4777 -> [AS4608] -> AS4777 -> (X)AS2516 -> (X)AS3549 -> AS43313 -> [AS43350]
Because the autonomous systems having AS2516 and AS3549 can see the traffic between AS9050 and comanche and the traffic between netfreak and politkovskaja (in this case 2 different AS's can see our full path), the circuit information is discarded and a new circuit is estimated.
Accepted values: 0, 2 |
| Do not use the public key step for the entry node when creating circuits | FastFirstHopPK | When this option is disabled, AdvOR uses the public key step for the first hop of creating circuits. Skipping it is generally safe since we have already used TLS to authenticate the relay and to establish forward-secure keys. Turning this option off makes circuit building slower.
Note that AdvOR will always use the public key step for the first hop if it's operating as a relay, and it will never use the public key step if it doesn't yet know the onion key of the first hop. (Default: 1) |
| Download extra information about nodes | FetchUselessDescriptors | If set to 1, AdvOR will fetch every non-obsolete descriptor from the authorities that it hears about. Otherwise, it will avoid fetching useless descriptors, for example for routers that are not running. This option is useful if you're using the contributed "exitlist" script to enumerate Tor nodes that exit to certain addresses. (Default: 0) |
| Circuit length | CircuitPathLength | The number of nodes that are added to a circuit. A circuit length of 1 can only be used with routers that have the option AllowSingleHopExits set because AdvOR would connect directly to the exit node. A circuit having a length of 10 will be the slowest and the most unstable having many AS path intersections in it. The default value is 3. |
|
Banned Routers

|
| Displayed name | AdvOR.ini value | Action |
|---|
| Do not use exits that were blacklisted by MaxMind"s GeoIP | IdentityFlags | Enable this option when country restrictions enforced by some websites can't be bypassed because the website is using a GeoIP that has most exit nodes blacklisted. Accepted values: 0, 2048 (Default: 0). |
| Banned routers | ExcludeNodes
ExcludeExitNodes | A list of identity fingerprints, nicknames, country codes and address patterns of nodes to never use when building a circuit. |
|
Favorite Routers

|
| Displayed name | AdvOR.ini value | Action |
|---|
| Use only entry routers from favorites | StrictEntryNodes | If set, AdvOR will never use any nodes besides those listed as favorite routers for the first hop of a normal circuit. |
| Use only exit routers from favorites | StrictExitNodes | If set, AdvOR will never use any nodes besides those listed in favorites as favorite exits for the last hop of a normal exit circuit. Note that AdvOR might still use these nodes for non-exit circuits such as one-hop directory fetches or hidden service support circuits. |
| Priority of favorite nodes | FavoriteExitNodesPriority | The priority is a percent and it is used when selecting a random exit node to decide if an exit node from favorites will be selected when the option to use only nodes from favorites is disabled (default is 100) |
| Favorite routers | EntryNodes
ExitNodes | A list of identity fingerprints, nicknames, country codes and address patterns of nodes to use for the first hop and for the last hop in normal circuits. These are treated only as preferences unless the above restrictions are set. |
|
Circuit Build

|
| Displayed name | AdvOR.ini value | Action |
|---|
| Learn circuit build timeout | LearnCircuitBuildTimeout | If non-zero, we attempt to learn a value for CircuitBuildTimeout based on timeout history. (Default: 1) |
| Circuit build timeout | CircuitBuildTimeout | Try for at most this number of seconds when building circuits. If the circuit isn't open in that time, give up on it. (Default: 1 minute.) |
| Circuit idle timeout until closing it | CircuitIdleTimeout | If we have kept a clean (never used) circuit around for this number of seconds, then close it. This way when AdvOR is entirely idle, it can expire all of its circuits, and then expire its TLS connections. Also, if we end up making a circuit that is not useful for exiting any of the requests we're receiving, it won't forever take up a slot in the circuit list. (Default: 1 hour.) |
| Stream timeout until trying a new circuit (seconds) | CircuitStreamTimeout | If non-zero, detach streams from circuits and try a new circuit if the stream has been waiting for this many seconds. If zero, use our default internal timeout schedule. |
| Cell scale factor | CircuitPriorityHalflife | This is the main parameter for picking circuits within a connection.
If this value is positive, when picking a cell to relay on a connection, we always relay from the circuit whose weighted cell count is lowest. Cells are weighted exponentially such that if one cell is sent 'CircuitPriorityHalflife' seconds before another, it counts for half as much.
If this value is zero, we're disabling the cell-EWMA algorithm.
If this value is negative, we're using the default approach according to either AdvOR or a parameter set in the consensus. |
| Maximum number of unused predicted open circuits | MaxUnusedOpenCircuits | The number of idle circuits that are built to make sure that enough circuits are available when needed. |
| Period to consider whether to build a new circuit | NewCircuitPeriod | Every time after this number of seconds consider whether to build a new circuit. (Default: 30 seconds) |
| Avoid reuse if a circuit is too old | MaxCircuitDirtiness | Feel free to reuse a circuit that was first used at most this number of seconds ago, but never attach a new stream to a circuit that is too old. (Default: 10 minutes) |
| Minimum circuit bandwidth rate | CircuitBandwidthRate | All routers that are chosen to be added to new circuits must have at least this minimum bandwidth rate. |
| Use same entry servers | UseEntryGuards
NumEntryGuards | If this option is set, we pick a few long-term entry servers, and try to stick with them. This is desirable because constantly changing servers increases the odds that an adversary who owns some servers will observe a fraction of your paths. |
| Node families | NodeFamilies | The Tor servers, defined by their identity fingerprints or nicknames, constitute a "family" of similar or co-administered servers, so never use any two of them in the same circuit. Defining a NodeFamily is only needed when a server doesn't list the family itself (with MyFamily). This option can be used multiple times. |
|
Associate Addresses

|
| Displayed name | AdvOR.ini value | Action |
|---|
| These addresses will always be associated with the same exit nodes | AddressMap | When a request for address arrives to Tor, it will rewrite it to newaddress before processing it. For example, if you always want connections to www.indymedia.org to exit via torserver (where torserver is the nickname of the server), use "www.indymedia.org www.indymedia.org.torserver.exit". |
| Tracked hosts | TrackHostExits | For each value in this list, AdvOR will track recent connections to hosts that match this value and attempt to reuse the same exit node for each. If the value is prepended with a '.', it is treated as matching an entire domain. If one of the values is just a '.', it means match everything. This option is useful if you frequently connect to sites that will expire all your authentication cookies (i.e. log you out) if your IP address changes. Note that this option does have the disadvantage of making it more clear that a given history is associated with a single user. However, most people who would wish to observe this will observe it through cookies or other protocol-specific means anyhow. |
| Exit node association expiration time | TrackHostExitsExpire | Since exit servers go up and down, it is desirable to expire the association between host and exit server after this number of seconds. The default is 1800 seconds (30 minutes). |
|
Hidden Services
|
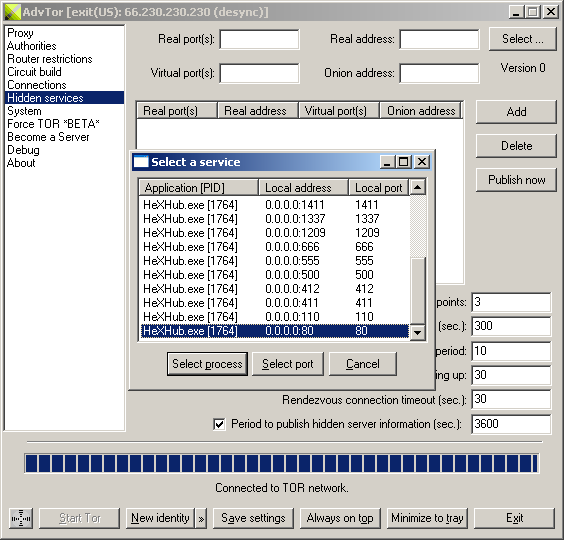
To start hosting a hidden service, start your server software that will host your hidden service and configure it to disable any settings that would cause it to reveal its real location (or, alternatively, you can intercept it). You start hosting a hidden service when you add it to the list of hidden services. Your service will be accessible through its associated .onion address (you may need to configure this .onion address in the server software you use).
To add a new hidden service, you can enter a "real port" value or you can click "Select ..." to select all ports opened by an application or a particular port that will be shared as a virtual port.
| 
|
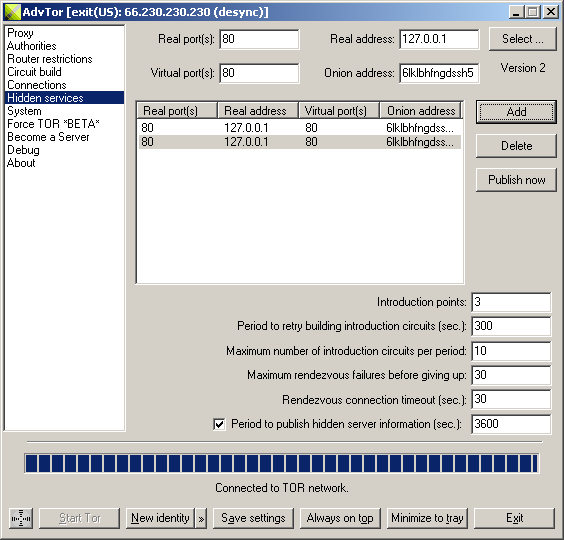
To register your hidden service, click "Add". If you have entered a prefix for your .onion address, AdvOR will try to generate an address that starts with that prefix. The address generator can be stopped anytime and you can use the best matching address that was shown when you stopped it.
| 

|
If you don't want a specific prefix for your address, you can leave the address field blank and AdvOR will use the first address it generates. An .onion address that is generated will be added to your hidden services list.
| 
| |
For an easier renaming, each hidden service is assigned a hidden service local key which will form a prefix for file names related to that hidden service. If AdvOR.exe is renamed, all saved files that have "AdvOR" prefix in their name must be renamed to replace "AdvOR" with the new name (including AdvOR.dll).
|
| Displayed name | AdvOR.ini value | Action |
|---|
| Introduction points | NumIntroPoints | Try to maintain this many intro points per service if possible. |
| Period to retry building introduction circuits | IntroCircRetryPeriod | If we can't build our intro circuits, don't retry for this long. |
| Maximum number of introduction circuits per period | MaxCircsPerPeriod | Don't try to build more than this many circuits before giving up for a while. |
| Maximum rendezvous failures before giving up | MaxRendFailures | How many times will a hidden service operator attempt to connect to a requested rendezvous point before giving up. |
| Rendezvous connection timeout | MaxRendTimeout | How many seconds should we spend trying to connect to a requested rendezvous point before giving up. |
| Period to publish hidden service information | RendPostPeriod
PublishHidServDescriptors | Every time the specified period elapses, AdvOR uploads any rendezvous service descriptors to the directory servers. This information is also uploaded whenever it changes. (Default: 20 minutes) |
|
Become a Server

|
The OR network relies on volunteers to donate bandwidth. The more people who run relays, the faster the OR network will be. If you have at least 20 kilobytes/s each way, please help out by configuring Advanced Onion Router to be a relay too. To do this, you must enter a port for your relay (default port is 9050). You are hosting an onion router when directory servers have your address in the list they share for OR clients (they may not immediately update their lists with your service).
|
| Displayed name | AdvOR.ini value | Action |
|---|
| Port | ORPort | Advertise this port to listen for connections from clients and servers. |
| Local address | ORListenAddress | Bind to this IP address to listen for connections from clients and servers. If you specify a port, bind to this port rather than the one specified in ORPort. (Default: 0.0.0.0) This directive can be specified multiple times to bind to multiple addresses/ports. |
| Nickname | Nickname | Set the server's nickname to 'name'. Nicknames must be between 1 and 19 characters inclusive, and must contain only the characters [a-zA-Z0-9]. |
| Contact information | ContactInfo | Administrative contact information for server. This line might get picked up by spam harvesters, so you may want to obscure the fact that it's an email address. |
| Node's advertised address | Address | The IP address or fully qualified domain name of this server (e.g. moria.mit.edu). You can leave this unset, and AdvOR will guess your IP address. |
| Don't do self-reachability testing | AssumeReachable | This option is used when bootstrapping a new Tor network. If set to 1, don't do self-reachability testing; just upload your server descriptor immediately. If AuthoritativeDirectory is also set, this option instructs the dirserver to bypass remote reachability testing too and list all connected servers as running. |
| Act as a bridge | BridgeRelay | Sets the relay to act as a "bridge" with respect to relaying connections from bridge users to the Tor network. Mainly it influences how the relay will cache and serve directory information. Usually used in combination with PublishServerDescriptor. |
| Make country statistics | BridgeRecordUsageByCountry | When this option is enabled and BridgeRelay is also enabled, AdvOR keeps a per-country count of how many client addresses have contacted it so that it can help the bridge authority guess which countries have blocked access to it. (Default: 1) |
| Refuse exit streams from unknown relays | RefuseUnknownExits | If this option is enabled, exit streams from OR's that are not known relays are dropped. Accepted values: 0 (never refuse), 1 (always refuse), auto (do what the consensus says, defaulting to 'refuse' if the consensus says nothing). Default value: auto. |
| Circuit timeout when entering hibernation | ShutdownWaitLength | When we enter hibernation and we're a server, we begin shutting down: we close listeners and start refusing new circuits. After this number of seconds, we exit. (Default: 30 seconds) |
| Maximum onionskins queued to decrypt | MaxOnionsPending
NumCpus | If you have more than this number of onionskins queued for decrypt, reject new ones. (Default: 100) |
Accept only these addresses
Banned IPs | ExitPolicy | Set an exit policy for this server. Each policy is of the form "accept|reject ADDR[/MASK][:PORT]". If /MASK is omitted then this policy just applies to the host given. Instead of giving a host or network you can also use "*" to denote the universe (0.0.0.0/0). PORT can be a single port number, an interval of ports "FROM_PORT-TO_PORT", or "*". If PORT is omitted, that means "*".
For example,accept 18.7.22.69:*
reject 18.0.0.0/8:*
accept *:*" |
would reject any traffic destined for MIT except for web.mit.edu, and accept anything else.
To specify all internal and link-local networks (including 0.0.0.0/8, 169.254.0.0/16, 127.0.0.0/8, 192.168.0.0/16, 10.0.0.0/8, and 172.16.0.0/12), you can use the "private" alias instead of an address. These addresses are rejected by default (at the beginning of your exit policy), along with your public IP address, unless you set the ExitPolicyRejectPrivate config option to 0. For example, once you've done that, you could allow HTTP to 127.0.0.1 and block all other connections to internal networks with
accept 127.0.0.1:80
reject private:* |
though that may also allow connections to your own computer that are addressed to its public (external) IP address. See RFC 1918 and RFC 3330 for more details about internal and reserved IP address space.
This directive can be specified multiple times.
Policies are considered first to last, and the first match wins. If you want to _replace_ the default exit policy, end your exit policy with either a reject *:* or an accept *:*. Otherwise, you're _augmenting_ (prepending to) the default exit policy. The default exit policy is:
The default exit policy used by Tor is:reject *:25
reject *:119
reject *:135-139
reject *:445
reject *:563
reject *:1214
reject *:4661-4666
reject *:6346-6429
reject *:6699
reject *:6881-6999
accept *:* |
|
| Publish | PublishServerDescriptor | This option is only considered if you have an ORPort defined. You can choose multiple arguments, separated by commas.
If set to 0, AdvOR will act as a server but it will not publish its descriptor to the directory authorities. (This is useful if you're testing out your server, or if you're using a controller that handles directory publishing for you.) Otherwise, AdvOR will publish its descriptor to all directory authorities of the type(s) specified. The value "1" is the default, which means "publish to the appropriate authorities". |
|
Private Identity

|
| Displayed name | AdvOR.ini value | Action |
|---|
| Generate new identity seeds used to randomize identity-specific information | IdentityFlags | Identity-specific generators for HTTP headers and for nicknames use identity seeds to ensure constant values during identity life time. |
| Reinitialize the global SSL context | IdentityFlags | Delete all SSL certificates that were used with SSL connections and generate new ones. All new connections will use the new SSL context. |
| Close all connections and destroy all circuits | IdentityFlags | Prevent mixing traffic that belongs to different identities. |
| Expire all circuits | IdentityFlags | Old circuits are no longer re-used for new connections. |
| Expire temporary address maps (tracked hosts) | IdentityFlags | Re-map all temporary address maps to new exits. |
| Delete cookies saved by processes that had OR connections | IdentityFlags | All processes that had HTTP OR connections and are still active are identified and their cookies and DOM storage (HTML5 cookies) are deleted. |
| Delete Flash Player's cookies, local storage data and history | IdentityFlags | Some websites may use some of Flash Player's features ("supercookies") to track their visitors. |
| Delete cookies stored by Microsoft Silverlight | IdentityFlags | Silverlight cookies may also contain tracking information. |
| Generate new Windows Media Player client ID | IdentityFlags | Your Windows Media Player client ID is saved to AdvOR-undo.reg and the file is not overwritten. If some licensed material is no longer playable because of changing your unique ID, double click the .reg file to restore it. |
| Show a completion MessageBox | IdentityFlags | Show a MessageBox to confirm that all the events related to changing your identity that blocked AdvOR have completed and that the AdvOR window is responsive again. |
| Every [time_interval] change my IP or my identity | IdentityFlags
IdentityAutoChange | This option enables automatic IP/identity changes. If a time interval is set, AdvOR will change your IP or your identity automatically according to your settings. When changing only the IP, all existing circuits are expired to cause new ones to be built having a newly selected IP and no other identity-specific information is changed; existing connection that use an older IP are not closed. When changing the identity, all your configured event handlers will be called and all your plugins that handle identity changes are notified.
Your new IP is chosen according to the exit selection algorithm you've set on the exit node selection dialog (for example, to have successive IPs from the exit list sorted by node name, sort the exit list by node name and enable the option to use consecutive exits from that list in that order, see Basic commands -> New identity). |
|
Version 0.3.0.0 introduces some experimental new features related to deleting cookies. Unlike other cookie deleters, we expect that all programs that need OR connections are still running and we expect to continue using them after deleting their cookies without affecting other instances that didn't have OR connections. The following browsers are currently supported (alphabetical order):
- Chrome
A process that uses chrome.dll is detected as Chrome. Chrome saves HTTP cookies to %localappdata%\Google\Chrome\User Data\Default\Cookies and to %localappdata%\Google\Chrome\User Data\Default\Extension Cookies and HTML5 cookies to %localappdata%\Google\Chrome\User Data\Default\Local Storage\http*localstorage . When changing identities, Chrome's handles for these files are closed and these files are deleted.
- Firefox
A process that uses xul.dll is detected as Firefox. A procedure that deletes cookies from all Firefox versions in a safe way while it is still running is difficult to maintain because of API inconsistencies between versions. Any "testcookie.exe" downloaded from Mozilla.org which uses XPCOM works only with 1 version of Firefox and fails with missing exports on all other versions. Another way would be to find a JavaScript context stored by the JavaScript runtime library (the library is renamed every few versions) and to use it to call JS_CompileScript / JS_ExecuteScript. If we find this method to be better, next versions of AdvOR will implement it.
Currently, we search xul.dll for a function that uses the string "DELETE FROM moz_cookies", which is the function nsCookieService::RemoveAll() . To be able to call it, we need a CookieManager instance. Again, xul.dll is searched for CookieManager's UUID {AAAB6710-0F2C-11d5-A53B-0010A401EB10} and near it we have a pointer to a constructor which can be called to get an instance. To delete cookies from Firefox we call CookieManager->RemoveAll() .
- Internet Explorer
A process that uses wininet.dll also uses Internet Explorer's cookies. If we find the function ClearMyTracksByProcessW in inetcpl.dll we call it to delete them (IE 8+). Otherwise we use wininet functions to delete cookies saved by IE. If this fails, we ForceDelete() all cookie files and index.dat.
- Opera
A process that uses Opera.dll is detected as Opera. When possible, we call a function from Opera.dll to delete all cookies. The function is not exported, so a few known patterns are used to find it. If this fails, we detect which kind of installation is the Opera process that had OR connections - a normal installation or a portable one - and we delete all cookie files (HTTP and HTML5) from all known locations without affecting other existing installations that didn't have OR connections since the identity was changed to current identity.
- Safari
A process that uses CFNetwork.dll is detected as Safari. If possible, we call CFHTTPCookieStorageDeleteAllCookies(_CFHTTPCookieStorageGetDefault(0)); via remote threads when possible and from AdvOR process when remote threads can't be created. If this fails, HTTP and HTML5 cookies are deleted from all known locations used by Safari.
If the cookies were successfully deleted, you should see a message like this when clicking "New identity":
|
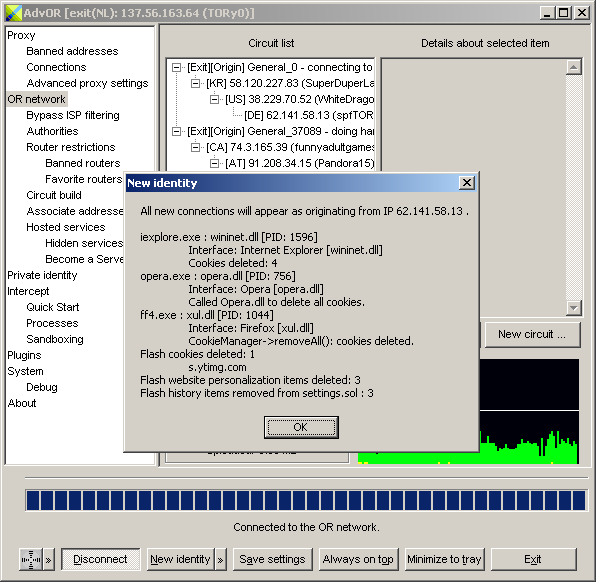
|
Quick Start
|
"Quick Start" is a list of favorite programs that Advanced Onion Router can start and intercept at startup. Each program can have its own private sandboxing settings. All program-specific sandboxing restrictions apply, and all programs started from the "Quick Start" menus / command line / window cannot access any real information that is restricted by these settings.
This is the "safe" way to start a program.
| 
|
To add a new program click "Add".
| 
|
You can browse to the location where the program you want to add is located, or you can write the name of the program if it is in a path that is listed in the PATH environment variable. The command line parameters are optional. To add a program, a program name must be given. The "Program name" is the name of the menu item that will be shown in the "Quick Start" menus.
The order of these menu items is the order they have on the list of applications and it can be changed using "Move up" and "Move down" commands.
|
Processes

|
The list of processes allows a quick way to release an intercepted process and/or to intercept a program that was started before starting Advanced Onion Router, or a program that is allowed to have have non-OR network activities during the same session. While sandboxing restrictions apply, the program may already have some restricted information it got before these restrictions were applied and it may send restricted information through the OR network. If you are not sure the program doesn't leak any information that can be used to uniquely identify you, consider starting it via "Quick Start".
|
Sandboxing

|
Sandboxing restrictions are used when a new process is intercepted. When a program is added to the "Quick Start" list, current sandboxing options are saved as the default settings for intercepting that program. To change the settings for an existing "Quick Start" entry, remove the program from the "Quick Start" list, change sandboxing options and re-add it. When using the "Processes" window to intercept an existing process, current sandboxing settings are used.
|
| Displayed name | AdvOR.ini value | Action |
|---|
| Local address | LocalHost | "Local address" is the address a program gets when trying to get your local IP. Here you can enter any fake address or hostname. |
| Fake local time | ForceFlags | The difference between your local time and someone else's local time can be used to trace your actions between different identities. Enable this option to prevent intercepted programs from using your real local time.
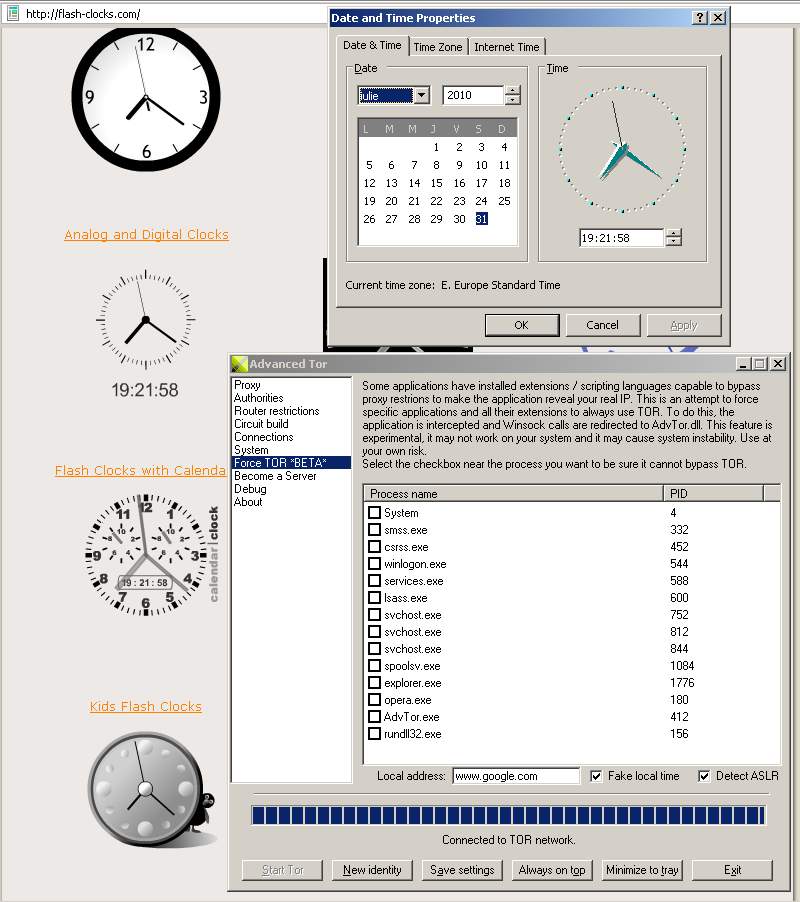
When a process is intercepted and the option to hide the real local time is enabled, the process can no longer get your real local time. All the time stamps the program can use, send and/or save will be fake.
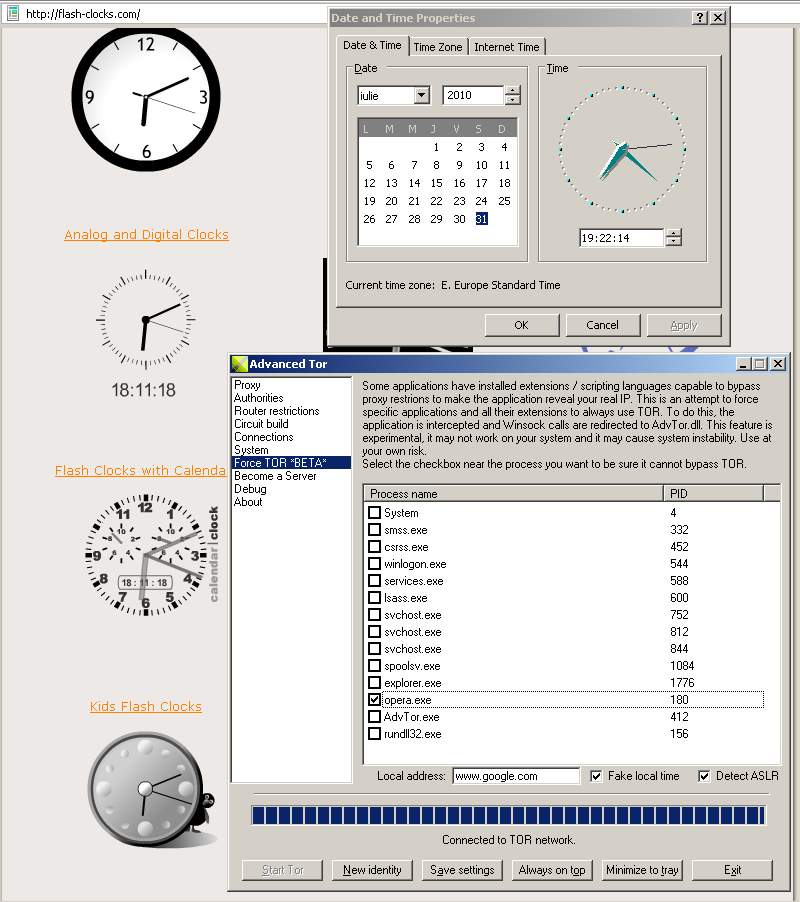
Accepted values: 0, 2 |
| Resolve only to fake IPs | ForceFlags | Fake IPs are within the 255.16.* range and are never sent through the OR network. Fake IPs are replaced with initial addresses when sending connection requests to exit nodes. Fake IPs are also used when a program tries to resolve an .onion address because .onion addresses cannot be resolved to an IP.
Accepted values: 0, 8 |
| Disallow non-TCP sockets | ForceFlags | Enable this option to make sure your real IP is not leaked when the program is using unsupported protocols.
Accepted values: 0, 16 |
| Exclusive exit | ForceFlags | Use this option to always exclude exit nodes that are currenly used by other programs to make sure the same exit node cannot know what you do with 2 different programs or instances of the same program.
Accepted values: 0, 64 |
| Change program's icon while it is intercepted | ForceFlags | When a program is intercepted its icon is changed by AdvOR.dll to help identifying intercepted processes. As an example, when intercepting Internet Explorer, the icon will be changed like in the following pictures:
 = Internet Explorer is not intercepted or it was released. = Internet Explorer is not intercepted or it was released. = Internet Explorer was intercepted successfully. = Internet Explorer was intercepted successfully. = AdvOR redirected a new connection request made by Internet Explorer. = AdvOR redirected a new connection request made by Internet Explorer.
Accepted values: 0, 32 |
|
Plugins

|
| Displayed name | Action |
|---|
| Plugin list | The list of plugins that were found in the AdvOR-plugins directory. To install a new plugin, copy it to the AdvOR-plugins directory and click "Rescan" to add it to this list. |
| Rescan | Search for newly installed plugins, add them to the list of plugins and try to load them if possible. |
| Remove | Remove a plugin from the list of plugins; the plugin is no longer used by AdvOR until you click "Rescan" to re-add it. |
| Reload | Unload a plugin, load it again and call its initialization procedures. |
| Unload | Disable a plugin |
| Rights | Limit the actions a plugin can do. The following rights are supported:
- Configuration page = the plugin is allowed to have a named configuration dialog that is added to the "Plugins" tree.
- Save settings to AdvOR.ini = the plugin can use AdvOR's functions to save/reload its settings to/from AdvOR.ini.
- Filter client traffic = the plugin can intercept the traffic made by a client and can alter it.
- Change address maps = the plugin can redirect an address somewhere else or it can change the exit node that will be used to access it.
- Create OR connections = the plugin can connect to other addresses through the OR network with or without exclusivity keys.
- Accept clients = the plugin can be a local server that can accept and register client connections as if they were accepted and registered by AdvOR.
- Hidden service provider = the plugin can host hidden services; hidden services hosted by a plugin can be added multiple times to the list of hidden services.
- Intercept processes = the plugin can use AdvOR.dll to intercept and release processes.
|
| Move up, move down | Change the priority of selected plugin. First plugin has the highest priority. |
|
System

|
| Displayed name | AdvOR.ini value | Action |
|---|
| Advertised OS version | winver | When running a server, this is the OS that will be known by directory authorities. This OS version is also sent to all clients. |
| Advertised Tor version | SelectedTorVer | A list of recommended Tor versions is received from directory servers when updating network status information. You can write a specific Tor version number or you can select one from this list. By default, a random Tor version is selected every time AdvOR is started. The Tor version is sent to directory servers when registering a new router. This version is also sent to all clients that will have your router listed in their network information. |
| Language | Language | The language file that is used to display all settings and messages. The "Default" language is the built-in language or the last language file that was loaded until AdvOR is restarted. |
| Connect automatically | AutoStart | Connect to the OR network when AdvOR.exe is started.
Accepted values: 0, 1 |
| Minimize at startup | AutoStart | When AdvOR is started, minimize to tray the AdvOR window.
Accepted values: 0, 2 |
| Start with Windows | AutoStart | Add AdvOR to the Windows startup (HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run). Accepted values: 0, 4 |
| Use hardware acceleration for cryptographic functions | HardwareAccel | If set, try to use built-in (static) crypto hardware acceleration when available. (Default: 0) |
| Try to write to disk less frequently | AvoidDiskWrites | If set, try to write to disk less frequently than we would otherwise. This is useful when running on flash memory or other media that support only a limited number of writes. (Default: 0) |
| Control port | ControlPort | If set, AdvOR will accept connections on this port and allow those connections to control the AdvOR process using the Tor Control Protocol (described in control-spec.txt).
Note: unless you also specify one of HashedControlPassword or CookieAuthentication, setting this option will cause AdvOR to allow any process on the local host to control it. This option is required for many Tor controllers; most use the value of 9051. |
| Control address | ControlListenAddress | Bind the controller listener to this address. If you specify a port, bind to this port rather than the one specified in ControlPort. We strongly recommend that you leave this alone unless you know what you're doing, since giving attackers access to your control listener is really dangerous. (Default: 127.0.0.1) |
| Require authentication with password hash(es) | CookieAuthentication | If this option is, don't allow any connections on the control port except when the connecting process knows the contents of a file named "AdvOR-control_auth_cookie", which AdvOR will create in its data directory. This authentication method should only be used on systems with good filesystem security. (Default: 0) |
| Hot key - Hide / restore Advanced OR window | HotkeyRestore | The hot key that can be used to minimize / restore the AdvOR window. |
| Hot key - New identity | HotkeyNewIdentity | The hot key that can be used to change the identity. |
| Hot key - Intercept focused application | HotkeyIntercept | The hot key that can be used to intercept the active application. |
| Hot key - Release focused application | HotkeyRelease | The hot key that can be used to release the active application if it is intercepted. |
| Hot key - Hide all intercepted applications | HotkeyHideAll | The hot key that can be used to hide all the applications that were intercepted by current session of AdvOR. This will also hide the AdvOR windows and disable all hot keys. The HotkeyRestoreAll hot key is registered and it is the only hot key that remains available. All processes are optionally paused / suspended. (Default: "`") |
| Pause hidden applications | HotkeyHideAll | If this option is enabled, when a process is hidden by AdvOR, all of its threads are suspended until the hot key to un-hide it is pressed. This value is a bit flag for the HotkeyHideAll value. Accepted values: 8192 (bit 13). |
| Hot key - Un-hide and resume hidden applications | HotkeyRestoreAll | The hot key that can be used to restore the AdvOR window and all intercepted applications. If the option to pause hidden applications is enabled, their threads are resumed. All hot keys are re-registered. (Default: "Ctrl+Win+7", must be changed) |
| Close all connections opened by a process when intercepting it | Confirmations | If this option is set, and an application has active connections when it is intercepted, all connections are closed. When in indeterminate state, AdvOR will always ask before closing active connections opened by the application which is intercepted. Accepted values: 0 (don't verify connections), 4 (ask before closing connections), 8 (close active connections) |
| Show a confirmation dialog on exit | Confirmations | To prevent accidental close of the AdvOR window, AdvOR can ask if you are sure you want to exit. When AdvOR exits, all processes intercepted by it are released. This does not affect processes intercepted by another instance.
Accepted values: 0, 1 |
| Only when releasing processes | Confirmations | If this option is enabled, AdvOR will ask for confirmation before exiting only if there are processes intercepted by it that will be released. |
| Encrypt all settings using AES | | If this option is enabled, all configuration files are compressed and encrypted and saved to AdvOR.dat. To disable encryption, click "New password", don't enter any password and click "OK", and all configuration files are saved as plain-text and AdvOR.dat is deleted.

You can enter a password or select a portion of a file that contains the key that will be used as a password (for example, "C:\ntldr" offset 44573. When using a password file, make sure that the offset is not greater than the file size minus 4096.
When the configuration files are encrypted, AdvOR will ask for a password when trying to load AdvOR.dat and it will use that password to decrypt it. AdvOR cannot start if it can't decrypt its configuration files.
The compression method is gzip and the encryption algorithm is AES. |
|
Debug
|
| Displayed name | AdvOR.ini value | Action |
|---|
| Message list | | A list of warnings, errors, notifications, etc. that is updated by AdvOR in realtime. |
| Save to AdvOR.log | logging | If this option is enabled, all messages that are shown in the message list are saved to AdvOR.log. Accepted values: 0, 32768 |
| Auto-refresh | logging | If this option is disabled, the message list is no longer updated (the log file can still be updated with new messages when not updating the message list). Accepted values: 0, 16384 |
| Log level | logging | Show only the messages that have this log level or lower. |
| Filters | NotifyFilter |
Messages that contain filtered strings are not shown in the message list and are not saved to AdvOR.log. The message filter can be updated using this command or from the context menus (select a string in the message list, right click it and select "Filter").
Each filter must be entered on a new line.
 |
| Clear | | Clear the message list. This command does not alter the log file. |
|
System Tray Menus

|
| Displayed name | Action |
|---|
| Show window | Restore the AdvOR window and remove the system tray icon. |
| Intercept ... | Open the process finder dialog to select a window created by a process that will be intercepted. |
| Quick start | The "Quick start" menu contains all the applications that were added to the "Quick start" application list. Select an application from this menu to start it intercepted by AdvOR. |
| Release | This menu can be used to release a process that is intercepted by AdvOR. Select a process name to release it. |
| New identity | This option is similar to the "New identity" button. |
| Select IP | A list with favorite exit nodes and some random IPs that can be chosen as exits. When selecting an IP from this list, the identity is changed and the IP will be used as the only exit. |
| Save settings | Save all configuration files when AdvOR is not running from a read-only location. |
| Connect / Disconnect | Connect to the OR network or enter hibernation mode. |
| Exit | Release all processes that are intercepted and exit the program. |
|
Command Line
|
A list with command line parameters can be obtained when executing the command "AdvOR --help".
The following commands are supported:
| Option | Action |
|---|
| --start | Connects to OR network at startup |
| --minimize | Minimize at startup |
| --QuickStart "menu option" | Starts the application associated with requested QuickStart menu option using its saved interception parameters and command-line parameters |
| --exec [program path] | Execute and intercept at startup a program. If there already is an existing AdvOR instance, it will receive this parameter. |
| --read-only | Do not write any files to disk (assume running from a read-only / write protected disk) |
| --select-exit [IP|country] | Selects default exit to a router IP or a country |
| --verify-lng [file] | Verify if a language file has errors in it. On success, the number of lines that were successfully imported is shown in a message box.
The "file" parameter can be a language name or a language file name. |
| --no-seh | Disable AdvOR's built-in exception handler. By default, when an exception occurs, AdvOR will ask if a crash report (AdvOR-crash.txt) needs to be saved if the configuration files are not encrypted and AdvOR was not started with the "--read-only" parameter. |
| --option value | Updates a configuration option with a new value |
| --help | Displays a list with command line parameters that are accepted by current version of AdvOR and exit. |
|
Building Circuits
|
Since version 0.1.0.12, when selecting a value of 0 for "Maximum number of unused predicted open circuits", AdvOR will only build new circuits when they are actually needed, or when a new circuit is created from Network Information page.
| 
|
As an example, let's see how to manually build a circuit of 5 hops to open http://www.google.com . First, we go to "Network information" (or "OR network" for versions 0.3.0.0+) and we use "New circuit ..." to open the circuit builer dialog. We set a circuit path length of 5 hops and we use "Estimate new path" to see possible circuits that respect all configured restrictions.
| 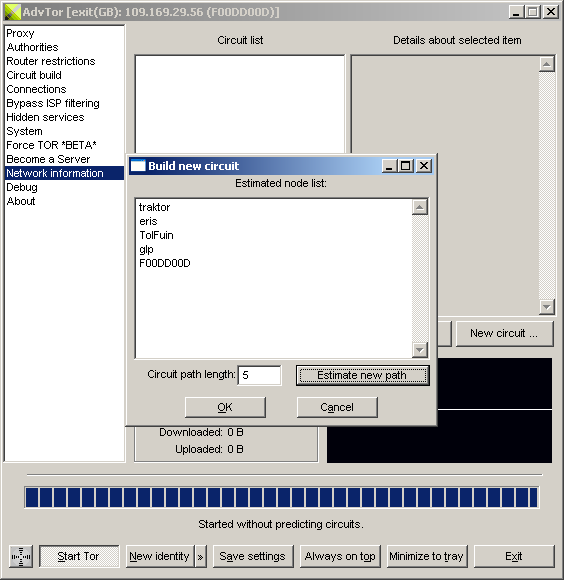
|
Having a node list, AdvOR will try to build a circuit using all nodes in their exact order. If any of requested routers is not available, or exit policies prevent a router from being used in a circuit having the configuration you specified, the circuit is destroyed. A circuit that was created successfully is shown as being in "open" state.
| 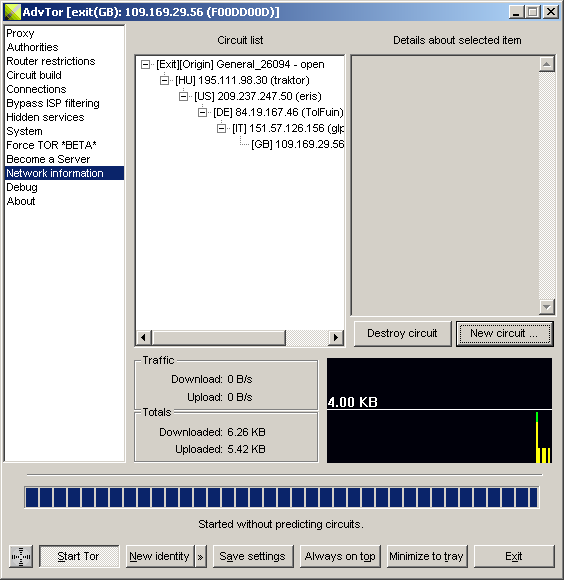
|
All application requests will use existing circuits if possible. If no circuits can handle a request, new circuits are created.
| 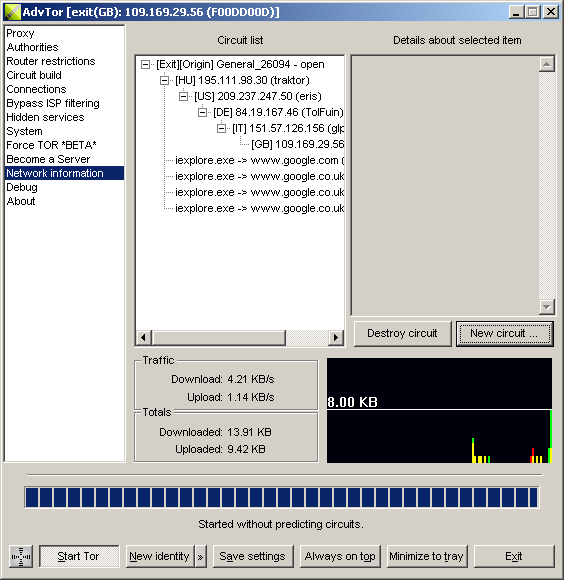
|
There are no restrictions for circuit path length when manually building a circuit and you can use this option to build a circuit with routers that would otherwise be excluded by your restrictions. However, the option to estimate a new good circuit may fail if circuit/router restrictions disallow all remaining routers before a path of specified length was created. For example, if the option to use only nodes from different countries in same circuit is enabled and a circuit path length of 300 is set, the function to estimate a good circuit will fail.
After creating a circuit, changing its priority to "High" will cause AdvOR to re-use it for all new connections. The same effect can also be achieved when the circuit has a normal priority and all other circuits have low priority - but in this case, when new circuits are built, they will have a normal priority by default.
To prevent a good circuit from expiration, its availability can be changed to "Never expires". To destroy a circuit immediately after all connections that use it are closed, the availability can be changed to "Expired". To destroy a circuit and close all connections that use it, click "Destroy circuit".
|
Support Information
|
For questions, bug reports, feature requests and other problems related to the use of AdvOR the following forums are available:
(no registration required: anonymous posting is allowed)
|
| |








































